Tor Browser Installation On Mac Os Hacker Proof
- Tor Browser Installation On Mac Os Hacker Proof Free
- Best Browsers For Mac Os
- Set Default Browser Mac Os
Sep 16, 2015 Here are instructions for installing Mac OS X in a VM and for installing Windows 10 in a VM. But it also presented Tor Browser-hacking malware to users of.
The encryption of files in the system is mandatory and can not be waived from the moment of installation, just like the communications, either through the browser or email. To encrypt the emails it uses the software Enigmail, while to navigate is Tor Browser. Jan 10, 2014 The bundle is based on the official Tor Browser Bundle with changes to make it work on older Mac OS X versions and the PowerPC architecture. Most notably, Qt is downgraded to the last Mac OS X 10.4 compatible version (4.7.4) and Firefox is patched. Sep 25, 2017 However, Tor Browser provides a way out to Mac users. Procedure to Download Tor Browser for Mac. To make internet browsing safe again some software are available such as Tor. By the use of Tor browser for Mac, a person’s web movements are disguised and routed through various voluntary operating systems from all over the world that are called. Tor is free and open-source software for enabling anonymous communication.The name derived from the acronym for the original software project name 'The Onion Router'. Tor directs Internet traffic through a free, worldwide, volunteer overlay network consisting of more than seven thousand relays to conceal a user's location and usage from anyone conducting network surveillance or traffic analysis.
Tails is a portable LIVE operating system that protects your privacy and helps you avoid censorship.
LEAVE NO TRACE. Tails uses the Tor network to protect your privacy online. It is based on Debian GNU/Linux.
Tor Browser Installation On Mac Os Hacker Proof Free
What is in TAILS 4.8 OS version?
Tails disabled the Unsafe Browser by default and clarified that it can be used to deanonymize you.
An attacker could exploit a security vulnerability in another application in Tails to start an invisible Unsafe Browser and reveal your IP address, even if you are not using the Unsafe Browser.
For example, an attacker could exploit a security vulnerability in Thunderbird by sending you a phishing email that could start an invisible Unsafe Browser and reveal them your IP address.
Such an attack is very unlikely but could be performed by a strong attacker, such as a government or a hacking firm.
Tails includes:
- Tor Browser with uBlock, a secure browser and an ad-blocker.
- Thunderbird with Enigmail, for encrypted emails.
- KeePassXC, to create and store strong passwords.
- LibreOffice, an office suite.
This is why we recommend that you:
- Only enable the Unsafe Browser if you need to log in to a captive portal.
- Always upgrade to the latest version of Tails to fix known vulnerabilities as soon as possible.
- Added a new feature of the Persistent Storage to save the settings from the Welcome Screen.
This feature is beta and only the additional setting to enable the Unsafe Browser is made persistent. The other settings (language, keyboard, and other additional settings) will be made persistent in Tails 4.9 (July 28).
Changes and updates
- Update Tor Browser to 9.5.1.
- Update Thunderbird to 68.9.0.
- Update Linux to 5.6.0. This should improve the support for newer hardware (graphics, Wi-Fi, etc.).
Fixed problems
- Fix the Find in page feature of Thunderbird.
- Fix shutting down automatically the laptop when resuming from suspend with the Tails USB stick removed.
- Notify always when MAC address spoofing fails and the network interface is disabled.
- Fix the import of OpenPGP public keys in binary format (non armored) from the Files browser.
Tails 4.8 Change logs
Security fixes
- Allow to disable the Unsafe Browser in the Welcome Screen. The Unsafe Browser can be used by exploits to deanonymize the Tails user.
- Upgrade Tor Browser to 9.5.1-build2.
- Thunderbird:
Upgrade to Thunderbird 68.9.0 (DSA-4702).
Disable unsafe MX automatic configuration method
Disable unsafe MS Exchange automatic configuration method. - Upgrade Linux kernel to linux-image-5.6.0-2 at 5.6.14-2
- Upgrade gnutls28-based packages to 3.6.7-4+deb10u4 (DSA-4697).
- Upgrade intel-microcode to 3.20200609.2~deb10u1 (DSA-4701).
Bugfixes
– Trigger emergency shutdown on resume when the boot device was removed while suspended.
– Thunderbird: make searching in messages (Find bar and Find in This Message) work again.
– Ensure Mac Spoofing Panic messages will be correctly displayed. udev may close child processes when a process associated with a rule (/etc/udev/rules) terminates so we wait for those processes before exiting.
– Wrap `seahorse-tool –import` so it is handled by `gpg –import`. This makes importing binary keys via GNOME
Files integration possible again.
Minor improvements and updates
– Upgrade to tor 0.4.3.5-1.
– Upgrade LibreOffice to 1:6.1.5-3+deb10u6.
– Upgrade VirtualBox guest modules to 6.1.10-dfsg-1.
– Append Unsafe Browser setting to WhisperBack debug info.
TAILS IS A FREE OPERATING SYSTEM
You can download Tails for free and independent security researchers.
System Requirements To Download Tails as follow:
Hardware requirements:

- A USB stick of 8 GB minimum or a DVD recordable.
- All the data on this USB stick or DVD will be lost when installing Tails.
- The possibility to start from a USB stick or a DVD reader.
- A 64-bit x86-64 compatible processor:
Download Tails 4.8
If you don’t need installation or upgrade instructions, you can download Tails 4.5 directly:
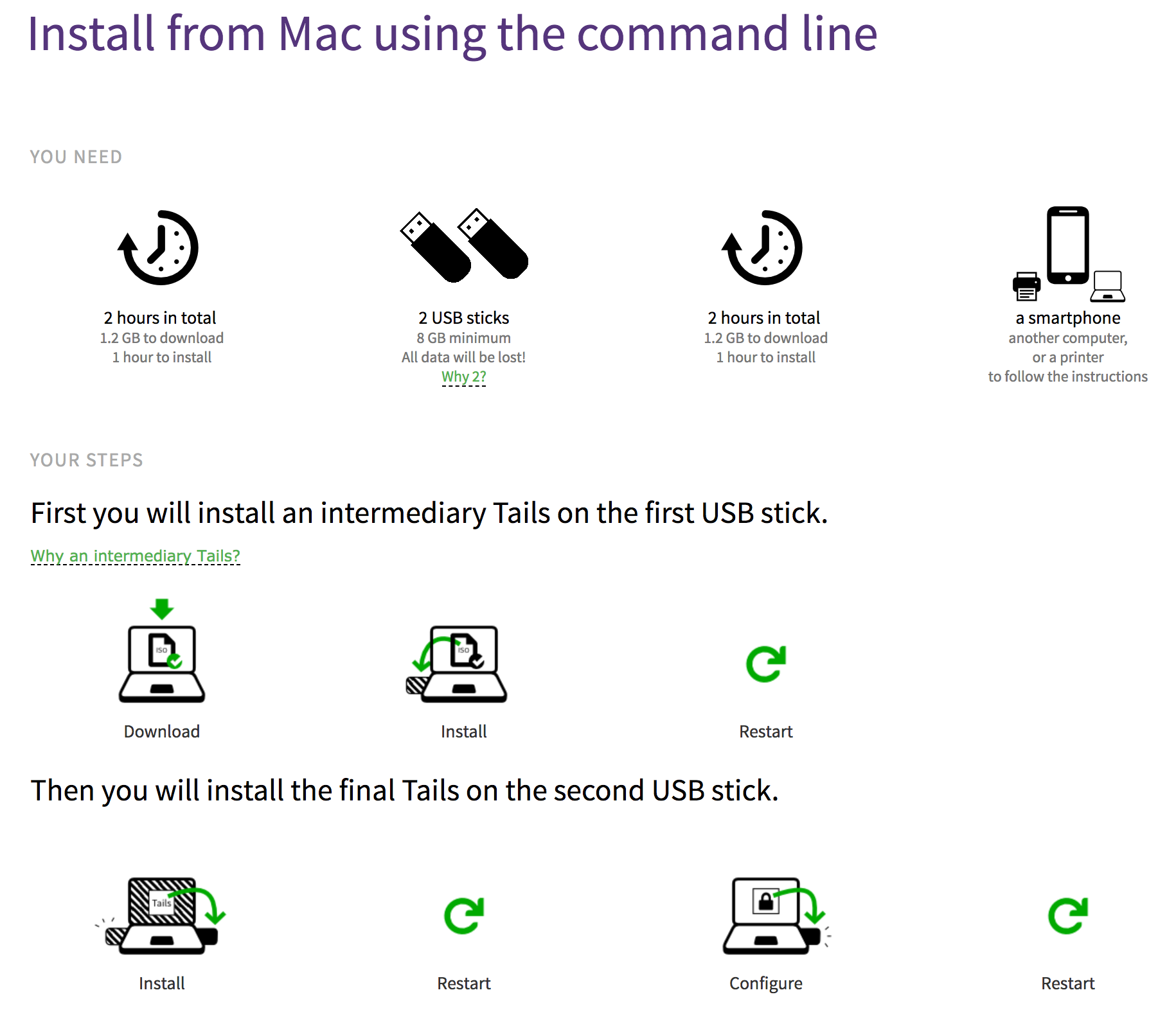
To install Tails on a new USB stick
Get connected
If you are in a country where Tor is blocked, you can configure Tor to connect to a bridge during the setup process.
Select 'Tor is censored in my country.'
If Tor is not censored, one of the most common reasons Tor won't connect is an incorrect system clock. Please make sure it's set correctly.
Read other FAQ's at our Support Portal
Stay safe
Please do not torrent over Tor.
Tor Browser will block browser plugins such as Flash, RealPlayer, QuickTime, and others: they can be manipulated into revealing your IP address.
We do not recommend installing additional add-ons or plugins into Tor Browser
Plugins or addons may bypass Tor or compromise your privacy. Tor Browser already comes with HTTPS Everywhere, NoScript, and other patches to protect your privacy and security.
Check out the Tor Browser manual for more troubleshooting tips.
Stand up for privacy and freedom online.
Best Browsers For Mac Os
We're a nonprofit organization and rely on supporters like you to help us keep Tor robust and secure for millions of people worldwide.